| Table of Contents |
|---|
2022-12-08 BGBU APAC TF Meeting
7.00 UTC = 23:00 PT = 8:00 CET = 11:30 IST = 16:00 Melbourne = 13:00 Thailand Zoom Meeting Link https://zoom.us/j/95121109567?pwd=UFBrWU5PcC9RZS9UaFg1UG81WGZZdz09 Meeting ID: 951 2110 9567 Passcode: 082179
MEETING RECORDING
Notes from the APAC Meeting are recorded in the Table below in green text
Attendees: Pyrou Chung; Nicky Hickman
| Time | Item | Lead | Notes |
| 5 mins |
| Nicky |
|
| 10mins | Intro's & Updates | Nicky | Update on Wallet TF - New Wallet Interactions & Patterns TF to work on patterns of design for wallets, aligns with Open Wallet Foundation (A Linux Foundation Project). Judith Fleenor has started recruiting, Accenture, Trinsic - needs to work for them as well. Alta Nel Rimma Perelmuter - Trust in Tech consultancy, focused on human centred design and trust that works for the digital economy. |
| 20mins | Harms TF update & next steps discussion | Nicky | Elisa Trevino is putting it on github Terms Wiki is done but - Glossary is not updating Judith Fleenor - We need to make sure that anyone who comments into the Public Review Process, then must join ToIP. Could be able to do so through gdocs as this is a paper not a specification. Can do on Github or gdocs. Phil Wolff Blog post missing contributors, call to action. Name on acknowledgements. Nicky Hickman to update Pyrou Chung - key is the so what question? Different perspective from people's perspective. EG school identity system for children - case study - how could we use the paper to structure and apply. How do you apply this framework to assist in improving their digital identity system - Nicky Hickman to do cheat sheet, practical guidance, then apply to school. International school in Thailand, have multiple jurisdictional requirements. Legal advice is they comply, but their rights are not respected especially for non-thai students. Technical view? Consent process but no data policy? Legal complications pre/post-covid. Their policy is not compliant with basic principles of privacy, failure consent = no school access. Pyrou wrote to the principle and asked the data to be removed and find a way for her son to access the school. Confusing issues: security, access control, attendance. Most of issues are not technical but are knowledge gaps, overlaps in user data for different and overlapping purposes. What is it used for? ie Purpose? Is public task applicable? In a private school public task is not applicable. Main issue is probably knowledge gaps - concerns about digital security among other parents, but most are unlikely to speak up. Especially Chinese, they are fleeing oppressive regime, so they devise work-around's - jump the gate! What are the protocols for intruder? If indeed it is for security. Biometric system. Thai government requires school to share the data with them for 'national security purposes' - risk for many who are in Thailand as they are at risk if identified. Diaspora from all over the world. Visa can be revoked, school can be implicated in this. Next Steps: January All Members Meeting - presentation open to others. Special Topic. X-pollination for Q1 - How can we work with you. inside ToIP Phil Wolff outreach beyond ToIP and convening, still need some form of ongoing community effort. Judith Fleenor must come from the WG., potential for SIG. Judith Fleenor consider outreach to other identity communities When is public review over? 30-60 days after the January All Members Meeting. BLOG - How and why should my company step up? Next communications committee meeting is next Friday 9th December - approvals can be done via email.
The following must be sent to HXWG channel, could step out of the acknowledgements for those named in blog post. (Nicky Hickman ) Nicky Hickman sort out glossary, also set up the document for comment in g-docs for non-github route. |
| 20mins | 2023 objectives | Kalin | meeting cadence & timing, APAC inclusion. Pyrou would like to continue to contribute to the community, Nicky Hickman to poll the APAC members to find an alternative time. HX focus on Wallet TF Business Scenarios workshop? |
| 5mins | AOB |
2022-11-24 BGBU APAC TF Meeting
...
| Time | Item | Lead | Notes |
| 5 min | Welcome & antitrust notice Agenda review | Nicky | Antitrust Policy Notice: Attendees are reminded to adhere to the meeting agenda and not participate in activities prohibited under antitrust and competition laws. Only members of ToIP who have signed the necessary agreements are permitted to participate in this activity beyond an observer role. |
| 10mins | New intro's & updates | Turing Institute Trustworthy Identities Conference - Decentralization & Harms a constant strand, | |
| 25 mins | New Arc | Nicky | Considering feedback and comments on the current drat of the white paper - suggested new arc/perspective as an alternative to 'ssi harms'
Actually the far side of the moon is not dark at all, but it is different from the near side. See The far side of the Moon, photographed by Apollo 16 in 1972. It is much more crater-ridden than the near side of the Moon. Source https://en.wikipedia.org/wiki/Far_side_of_the_Moon. Not all of the far side of the moon is invisible from earth due to a phenomenon known as libration "In lunar astronomy, libration is the wagging or wavering of the Moon perceived by Earth-bound observers and caused by changes in their perspective. It permits an observer to see slightly different hemispheres of the surface at different times. It is similar in both cause and effect to the changes in the Moon's apparent size due to changes in distance. " This paper is like the Apollo 8 astronauts who were the first humans to see the far side in person when they orbited the Moon in 1968. We are just mapping that side of digital identity which we all know is there and contributing to opening up debate and developing robust legal, technical, human experience and governance mechanisms for addressing this problem. e.g. https://privacyinternational.org/advocacy/4945/letter-global-csos-world-bank "We, the undersigned civil society organizations and individuals, urge the World Bank and other international organizations to take immediate steps to cease activities that promote harmful models of digital identification systems (digital ID). "
|
| 15mins | Potential Titles | Nicky | From discussion in HXWG
From story Arc Mapping the Far Side of the Moon: A new framework for understanding and mitigating the human harms of digital identity systems; ‘Overcoming the challenges of human harms from in digital identity ecosystems’ The Apollo 16 Paper: Considering human harms in digital trust ecosystem design / digital identity systems Vision based: Do no harm: creating digital identity systems that serve the public good On track for finishing 2nd draft end next week Darrell O'Donnell and Christine Martin to do Foreward |
...
| Time | Item | Lead | Notes |
| 5 min | Welcome & antitrust notice Agenda review | Nicky | Antitrust Policy Notice: Attendees are reminded to adhere to the meeting agenda and not participate in activities prohibited under antitrust and competition laws. Only members of ToIP who have signed the necessary agreements are permitted to participate in this activity beyond an observer role. |
| 10mins | New intro's & updates | Updates from HXWG - Meeting page Reviewed & considered the consent question: Mark Lizar and Phil Wolff are working on this, may be extendend from blog post to paper of series of 'nuggets' that discuss questions such as 'how to orchestrate consents within a digital trust ecosystem?'; This is the intersect w/ISWG Phil Wolff commented that smaller pieces to prompt discussion was more productive than long papers or set pieces Nicky Hickman is focused on producing a draft Whitepaper for SSI Harms this week sankarshan and Pyrou will be hosting a discussion at the forthcoming APAC IIW on SSI Harms Pyrou commented that next week is International Indigenous People's Week, 10 events in the region including meetings with legislators & policy makers around law making, others are celebrations. If indigenous people have self sovereign rights, how does that affect our work. Feels like progress, a platform for open discussion with politicians is Environmental harms & battle for resources & challenges of climate crisis - disconnects | |
| 40mins | Reviewing sections of paper | Nicky | The logic of harms - good starting point - but livelihoods approach is not necessarily useful for this paper. Nicky Hickman to introduce Pyrou Chung to Kelly Cooper to develop Case Study including a village community as a persona. The split of papers - makes sense otherwise too long |
| 5mins | AOB & Actions | Nicky |
...
| Time | Item | Lead | Notes | ||||
| 5 min |
| Nicky |
| ||||
| 10mins | Intro's & Updates | Nicky | Eric Welton- discussions with Myanmar Responsible Business Coalition - tricky situation with hostile relationships in government - establishing a biometric identity - difficult choice as someone is going to do it. Can we do it in a more responsible, less harmful way. May be useful to have a session on this in this group. Difficult ethical questions for the team. Interesting presentation on how digital ID can be abused. sankarshan- biometric topic seems to be settling down from aid organisations - have to use biometrics, main focus is now on mitigating harms. Myanmar, Afghanistan and other examples. Uganda for example, optimistic programme, under-enrollment. (the harms of untrustworthy systems) - now starting w/genetic profiling! "The genie is out of the bottle" Jo Spencer Activity on NSW gov initiative - driving license initiative hacked, DNA & biometrics further reinforce the argument.
sankarshanMinimisation is not suitable for some interactions, e.g. Medical Records - much more important for secure and trustworthy data payload / exchange. Also Financial Transactions not very well suited to VC's. Jo Spencer use of verifiable presentations which present derived data. sankarshan taxonomy & semantics - quality & classification of data also needed VC's are not the solution for many forms of data. Biggest harm is derived data sets from small data sets. Eric Welton - Use cases - all non-cash transactions will be exposed to government, e.g. national security / tax collection is given as purpose coming in ??. Remember problems of correlation highlighted by Daniel Hardman Also use case of VCs to convey health information - presentation that key emergency information for medical purposes (e.g. in accident) - could use biometrics to unlock the data for emergency responders. VC is a PDF - convenience / emergency service. Similar to ICE contact, could have ICE Credential. Could be linked to IATA - Good Health Pass sankarshan Must be freeform data. Accept that this is a new attack surface. John Phillips Humanitech conference - could be some good material & input to this discussion. Great discussion and material. I'm now seeing an obvious connection between this work, and the work of the Humanitech organisation here in Australia (founded by the Australian Red Cross) who have been thinking about how they might "ensure frontier technologies benefit people and society". I was at, and spoke briefly, at their 2022 conference (https://humanitechsummit.org/2022/) - they've been considering the potential harms of the mis-application of frontier technology for some time. | ||||
| 5mins | Actions | Nicky |
| ||||
| 15mins | AGENCY | Nicky | Review of notes and insights from the AGENCY talk at HXWG last week. Here is the wiki page On fake news (and news) there's a good 20 mins conversation from Davos hosted by Polkadot -
Rumsfeld Structure to scope "Reports that say that something hasn't happened are always interesting to me, because as we know, there are known knowns; there are things we know we know. We also know there are known unknowns; that is to say we know there are some things we do not know. But there are also unknown unknowns—the ones we don't know we don't know. And if one looks throughout the history of our country and other free countries, it is the latter category that tends to be the difficult ones.[1]" (Source: Wiki) Also for discussion see this Miro Board
| ||||
| 20mins | Storyboard Next Steps | Phil | NEW (Google Slides): https://docs.google.com/presentation/d/1Y404nJpSOkJFK5pc2aYUmJtrXtCkwcx-eIMC9ZMC0DU/edit?usp=sharing Phil has transferred to a G-DOC https://docs.google.com/document/d/151cqN0HY-ECmGwcS_SSBCeCHtszuwGyQebLRJq8sODA/edit?usp=sharing which contains the same material but in a doc format | ||||
| 5mins | AOB | Nicky |
...
| Time | Item | Lead | Notes |
| 5 min |
| Darrell |
|
| 5 mins | Intro's new members & Updates | All | Updates
|
| 5 mins | Update on Actions from Previous Meetings | All |
|
| 30 mins | Discussion Scope: Root Cause Analysis & Frameworks | Nicky | Scope & clarification from USA Call
Root Cause Analysis?
Possible Frameworks:
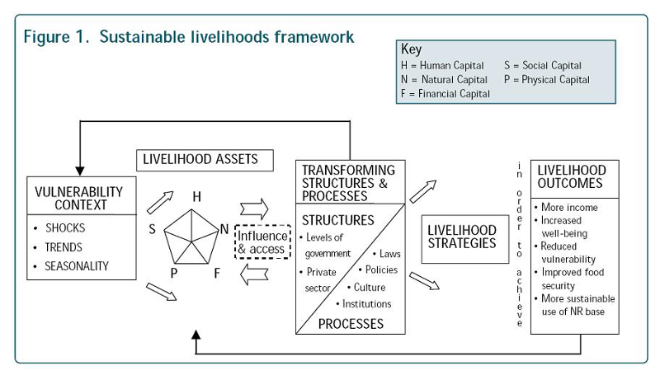
4. SECTOR-BASED - prioritizing the primary sectors of uptake that ToIP members want us to look at and which impact against sustainable livelihood outcomes Healthcare Public Sector National Identity & Legal Identification Financial Services & Fintech 5. OUTCOMES-BASED Sustainable Livelihoods framework . Based on the principle that your digital data is a livelihood asset, a new form of capital? Or a digital representation of other types of capital? Harms arise when the outcomes or consequences negatively impact positive livelihood outcomes
More likely a combination of a couple of these? Discussion - starting more messy and coming to frameworks, e.g. start with one harm and build out an approach of key questions:
Can also have ideation session - dropping a long list of harms - reference powerpoint storyboard - put in slack for other sto update then add one harm with above questions to get started. |
| 10 mins | Storyboard | Darrell | |
| 5 mins | Close & AOB | Nicky |
|
...
| Time | Item | Lead | Notes |
| 5 min |
| Darrell |
|
| 5 mins | Intro's new members & Updates | All | Phil Wolff - individual contributor at DIF and ToIP and sometimes Sovrin IoT, IEEE identity work also.- led several sessions on threat vectors and harms associated with digital ID. Oskar van Deventerleader at TNO and eSSIF lab (>50 sub-grantees). Leader on interop, also European Blockchain Service Infrastructure representing NL. Have developed prototype. At TNO ~20 people working on SSI, 4 working on standardization at DIF. Techruption project with banks, land registry, notaries, similar scope looking at harms. Coordinating
|
| 5 mins | Update on Actions from Previous Meetings | All |
|
| 10 mins | Oskar Insights | Oskar | Overview of insights from Oskar's work and blogs - where are the key gaps/issues? - perspectives on key deliverables / scope and direction for the group?
Rushing with eIDAS - on SSI - Danger is we all become 'vulnerable' people - we are not empowered, controlling your digital ID can sometimes undermine my rights. EG hotels that make me break the law by asking to copy my passport. Harms relate to many harms that can arise e.g. https://blockchain.tno.nl/blog/verify-the-verifier-anti-coercion-by-design/ Protections - e.g. chip in passport - but fingerprint data can only be accessed by authorised verifiers. - these protections are missing from SSI. Wants to see implementations: e.g. authorised verifier 5-6 items that all need implementation, standardisation and interop testing Does this change our deliverables? Supplier authentication, call centre use case especially outbound calling e.g. Bloqzone Gorilla use-case, I know who you are exclusion or discrimination if you don't accept data sharing - problem Knotty Problem: Privacy vs Access to food / services Rieks - one step back ie WHY do you need this data - data minimization tool, often not needed for business decision, also issuing information to be consumed by other gorillas (bring in Amos' work) KNOTTY Biz Problem conflicting regulatory requirements. Risk with SSI that we are going in a different direction because SSI gives higher assurances, now not only do you have to fill in the forms, now you can't lie about it and get it from an authorized source. Old LoA argument - economic resources and politics. Advise not focusing on excluded communities then risk that we ignore the issue that we all become vulnerable:
Different uses of persona, nature of harm and context - user research - better to talk to actual people rather than using persona, ethnography, interview people, e.g. those who have lived with harm. EG a black person obliged to add a photo indicating race, would harm professional career. Storytelling use of persona to make harms relatable - EG not defining gender, use of they, them pronouns in the group and research Remember SSI is transactions between two parties - relevance between the transactions that the two parties want to engage with. Assertion of our social norms considering what is harm? Harms only steming from those things which SSI is supposed to relate to. Could we simplify by focusing on Highlights any new DRiPHT introduced by use of decentralized architectures and SSI, and how they could be mitigated Over-identification problem - making it easy to add LoA3/4 creates new exceptional harms. END____ |
| 10 mins | Storyboard | Darrell | |
| 5 mins | Close & AOB | Nicky |
...
| Time | Item | Lead | Notes |
| 5 min |
| Darrell |
|
| 10mins | Intro's new members & Updates | All | |
| 5 mins | Update on Actions from Previous Meetings | All |
|
| 10mins | Review HXWG progress | All | - APAC Group to consider speakers. e.g. This is the group that we're connected to through our work with Swinburne University a few years ago: https://sigchi.org/ |
| 10 mins | Discussion on items raised in Slack & APAC meeting | Nicky |
1) Group of indigenous people - Pyrou Chung Eric - could be related to Family Unit below 2) Family unit: (Phil) A family where the notions of family aren't modeled where they live or travel. A polyamorous truple with kids and the six grand-parents. (intergenerational, doesn't conform to norms of marriage, complex guardianship) - West Africa polygamous families. Eric: Clans or groups in S Asia, 7 or 8 houses clustered together, kinship group. Variations on a theme - depends on kinship structures. Insight, many grandparents don't know their own age. Eric has found potential collaborators / folks on the ground who are able to help us build grounded persona
3) Children |
| 25 | Storyboard | Darrell | Outline Storyboard is here: https://docs.google.com/presentation/d/1KoWjJx8LMwqNHKhAs-gK1uLdDL6zniIR/edit?usp=sharing&ouid=102748924597224658467&rtpof=true&sd=true
Example from Eric - Living near a safe house for IDP (underground railroad) in west of Thailand (Korim) - He has all his papers and can move freely, he is becoming stateless so that he can get back into the camp in order to care for his elderly parents, familial obligations - giving up his legal identity to fulfill his duties. Corruptions in guards, violence associated with money and being able to leave the camp to work. Too strong an identity would prevent this. Harm of centralized model with biometrics = he is 'owned by the state' - can't remove yourself from the system. John: This is the group that we're connected to through our work with Swinburne University a few years ago: https://sigchi.org/ Eric: another group that is local to me, which may be helpful in identifying unique harms/risks is: https://kwahdao.org/ - their current director just graduated from law school and is one of their first students especially looking at stateless children. |
| 5 mins | Close & AOB | Nicky |
|
...
| Time | Item | Lead | Notes |
| 5 min |
| Darrell |
|
| 10mins | Intro's new members & Updates | All | Name change of group to 'Balancing the Good, The Bad & The Ugly' This has been posted on linked in, at an earlier time slot, so to be resolved for next meeting cycle. Christine Martin - work with Darrell at Continuum Loop. EA and topic of interest. |
| 5 mins | Update on Actions from Previous Meetings | All |
Observation: Sometimes the drive to design solutions for crisis situations, e.g. Ukranian Refugees can itself lead to unittended harms or consequences because of speed & emotion.
|
| 10 mins | Discussion on items raised in Slack & APAC meeting | Nicky |
3) Children: (Sankarshan) The topic of harms around minors in context of travel came about when we were noodling on the GHP Travel related recommendations. As in - whether adoption of SSI based patterns will inadvertently enable harms to be easier, higher primarily because of weak adoption of guardianship and identifier best practices. 1) Group of indigenous people - Pyrou Chung 2) Family unit: (Phil) A family where the notions of family aren't modeled where they live or travel. A polyamorous truple with kids and the six grand-parents. (intergenerational, doesn't conform to norms of marriage, complex guardianship) - West Africa polygamous families. Eric: Clans or groups in S Asia, 7 or 8 houses clustered together, kinship group. Variations on a theme - depends on kinship structures. Insight, many grandparents don't know their own age. See lessons from Aadhar. Main challenge is inability to understand how the design of the system was successful or failed, also depends on adoption, enforcement, liabilities. EG Financial crimes are better handled through stronger regulation and enforcement. Currently a reputational issue for SSI because of misunderstandings and perceptions. Raises common issues such as governance and its enforcement in decentralized systems and the rights/human dignity issues. Danger is that we create an inventory of risks with mitigations, but could be counter-productive, but in long run we need to design better ways of representing living entities in digital formats. Is there a need to uniquely identify humans, personhood. Is it possible to do so without being political? Must nevertheless start somewhere and narrow scope. Use persona as test bed to check our thinking. Start with one persona and encourage others to build their own and engage this way. Perhaps children as easy for all to relate to and understand. Groups to consider: Those that are biometrically impaired,
|
| 25 | Storyboard | Darrell | Outline Storyboard is here: https://docs.google.com/presentation/d/1KoWjJx8LMwqNHKhAs-gK1uLdDL6zniIR/edit?usp=sharing&ouid=102748924597224658467&rtpof=true&sd=true |
| 5 mins | Close & AOB | Nicky |
|
...
| Time | Item | Lead | Notes |
| 5 min |
| Darrell |
|
| 20mins | Intro's | All | Sankarshan - India, returning to ToIP following work absence, SSI Harms - harms created by solutionism and poor understanding, need to work through this topic to address Eric Welton - Thailand south of Myanmar border, been looking at SSI Harms for 5-6 years, because bulk of tech driven by heavily digitised communities (EU, USA) with civil liberties basis, but not the reality in countries like e.g. China, has SSI components but very centralised. Forcing view without asking people if they want to for example be financially included. No engagement, combined with new surveillance capabilities, many harms can arise, e.g. camera's. At the precipice of getting things done right or wrong. Pyrou Chung - Thailand Director at East West Mgt - Open Dev Initiative - focus on data governance meets tech meets human rights, one main focus related to Indigenous peoples for sovereign data rights includes identity, not allowed to assert their identity, so no existing rights within frameworks so if a new system comes in that doesn't take into consideration their right indigenous rights e.g. for accessing public services, could exacerbate existing Jo Spencer - (AUS) Initially drawn into the Guardianship WG realised that there was a model where we could put into place more certainty and controls with the right levels of trust and flexibility. Work in Sezoo with John Philips. Working with some parts of Gov. Indigenous identity a passion project, not the right people to do it. Once you have the tools, then can begin to tailor to needs of groups like indigenous peoples without the controls of government and surveillance capitalism. Not about the tech more about the social impact of what you are doing. Also some research w/ Universities around use of wallets. |
| 15 mins | Overview & Goals of the TF | All | Notes to ensure we include dissenting voices by having some outside sessions later on in the process
Open as to what happens once initial deliverables are provided Agree to focus on IIW for StoryBoard, and the stuff we are stuck on - where we have need for other views and help Keep the narrative - the tech won't save us!!! This is about humans, they are the builders of the good and bad stuff. 'No tech fix for the human condition!' APAC - Suggested change to Harms Mitigation Task Force. Example - Verifier pays issuer - what's the harm, what's the impact, what are the mitigations? Develop Persona to measure and manage harms/risk against. EG indigenous people, concept of collectivised identity is core to indigenous people, so we have a 'Persona Group' rather than a single individual, also link with Environment, e.g. things with digital identity, rivers in India, Uluru in Aus. How environment & lands are connected with identity of individuals and have their own (socio-centric vs ego-centric) - 'individual vs dividual'. (WRT respectful approaches to working with indigenous peoples, I've been impressed by the work of Terri Janke: https://www.terrijanke.com.au/true-tracks) Clash between two cultures e.g. Aus problem of indigenous incarceration problem. How can these interoperate when different social views of identity and ways of managing rights & accountabilities Example of Northern region crossing China, Laos, Myanmar, Thailand - very many different ethnic groups forced into mountains and e.g. Thai Union is forced upon them. Long history - yes identity is a political tool that is related to power & control. Consider land, connection, associations & movements of people. But note the cultural and spiritual connections to the land and deep within their psychographic identity. Also needs to be considered and catered for. Their own sovereign ability to govern the processes associated with technology. This is where governance comes into play regarding collectivised identity. Colonial narrative and mental models for example in forms of identity and governance models. Connection w/state services - collectivisation builds social capital and bargaining power w/state. Perhaps go further and find these folks to participate and help us build real case studies and examples. On the ground reality, need to be careful that we have real people in mind. |
| 15 mins | Discussion on next steps, plan | Nicky |
|
| 5 mins | Close & AOB | Nicky |
|
...
| Time | Item | Lead | Notes |
| 5 min |
| Darrell |
|
| 20mins | Intro's | All | Kaliya Young - Identity Women - IIW and 'Human First Tech' - advocating for more of these types of conversation, have threat model analysis paper . Naming harms of Web 1.0 & 2.0 Event Bart Suichies - No affiliation, active in SSI for 5-6 years, joined ToIP through SICPA. Interest in SSI in public sector, and use where active governance. Interested in figuring out where the lines are for what we can do as a community for solving societal problems. Paradox of powerful tools for dual use good / bad Kalin Nicolov - joined also as SICPA, currently co-chairing the HXWG - focused on connection point of HX design, interactions of ethics, incentive structures, points that are grey areas. Darrell O'Donnell - part of ToIP from beginning - focused on making it real and understanding harms. Affiliation - small boutique consultancy Shireen Mitchell - Here to have the conversation about harms - statelessness is only identifier we find racism, part of Human First Tech with Kaliya. Moments where we sit on the security line thinking about finance, but ignoring the impacts on 'real identity'. Some concerns with the white papers problem in defining people's identity by their vulnerability attributes Jacques Bikoundoublockchain developer, member of ToIP for 2 years, mainly involved in drafting GF documents, participated in CCI, interested because keen to understand how the technology can impact people Phil Wolffhere to contribute to the threat analysis & mitigate harms, possibly from a product management lens. Privacy advocate for 15 years, originally Oakland and now Pacific Northwest, consult for Wider Team on ID of things in healthcare. Led "Death to NSTIC" sessions at IIW to brainstorm and characterize threats to initiative success. Nicky: Freelancer Judith Fleenor, Director of Strategic Engagement for ToIP Jon Pinkes, technologist linked via Kaliya & IIW |
| 15 mins | Overview & Goals of the TF | All | Notes to ensure we include dissenting voices by having some outside sessions later on in the process
Open as to what happens once initial deliverables are provided Agree to focus on IIW for StoryBoard, and the stuff we are stuck on - where we have need for other views and help Keep the narrative - the tech won't save us!!! This is about humans, they are the builders of the good and bad stuff. 'No tech fix for the human condition!' |
| 15 mins | Discussion on next steps, plan | Darrell |
|
| 5 mins | Close & AOB | Darrell |
|
...